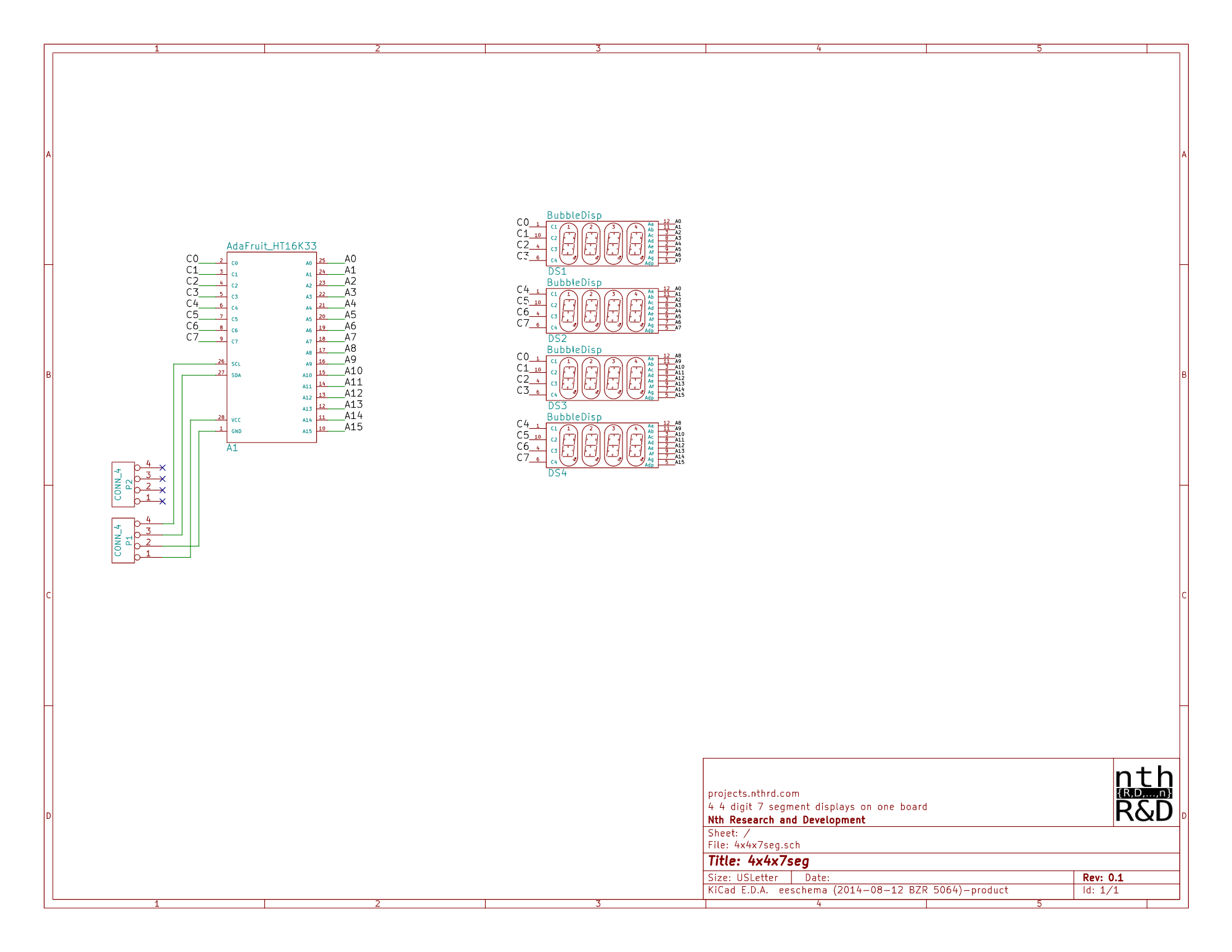
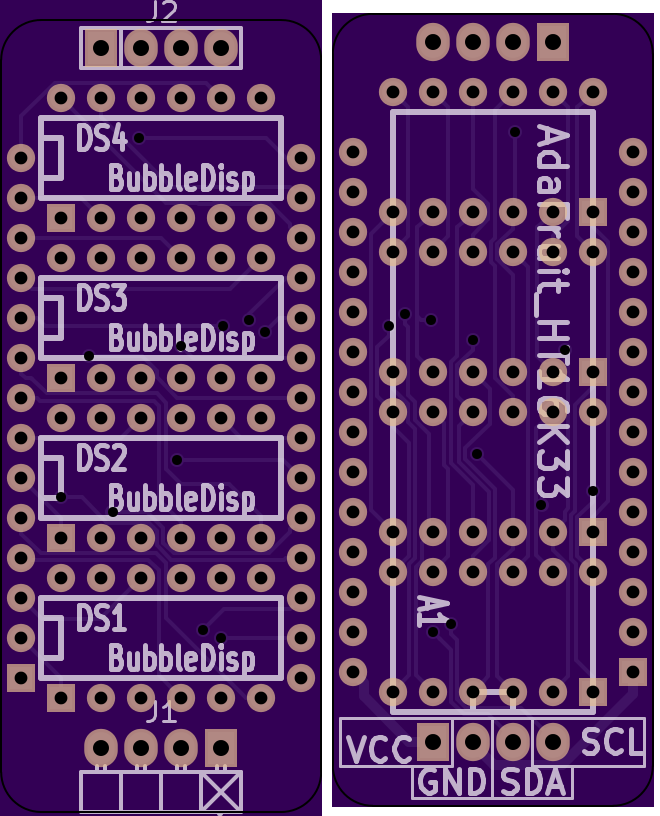
Projects
Conceptual Designs
Requirements gathering and system architecture projects.
Integrated Home System
Secure SmartHome Architecture
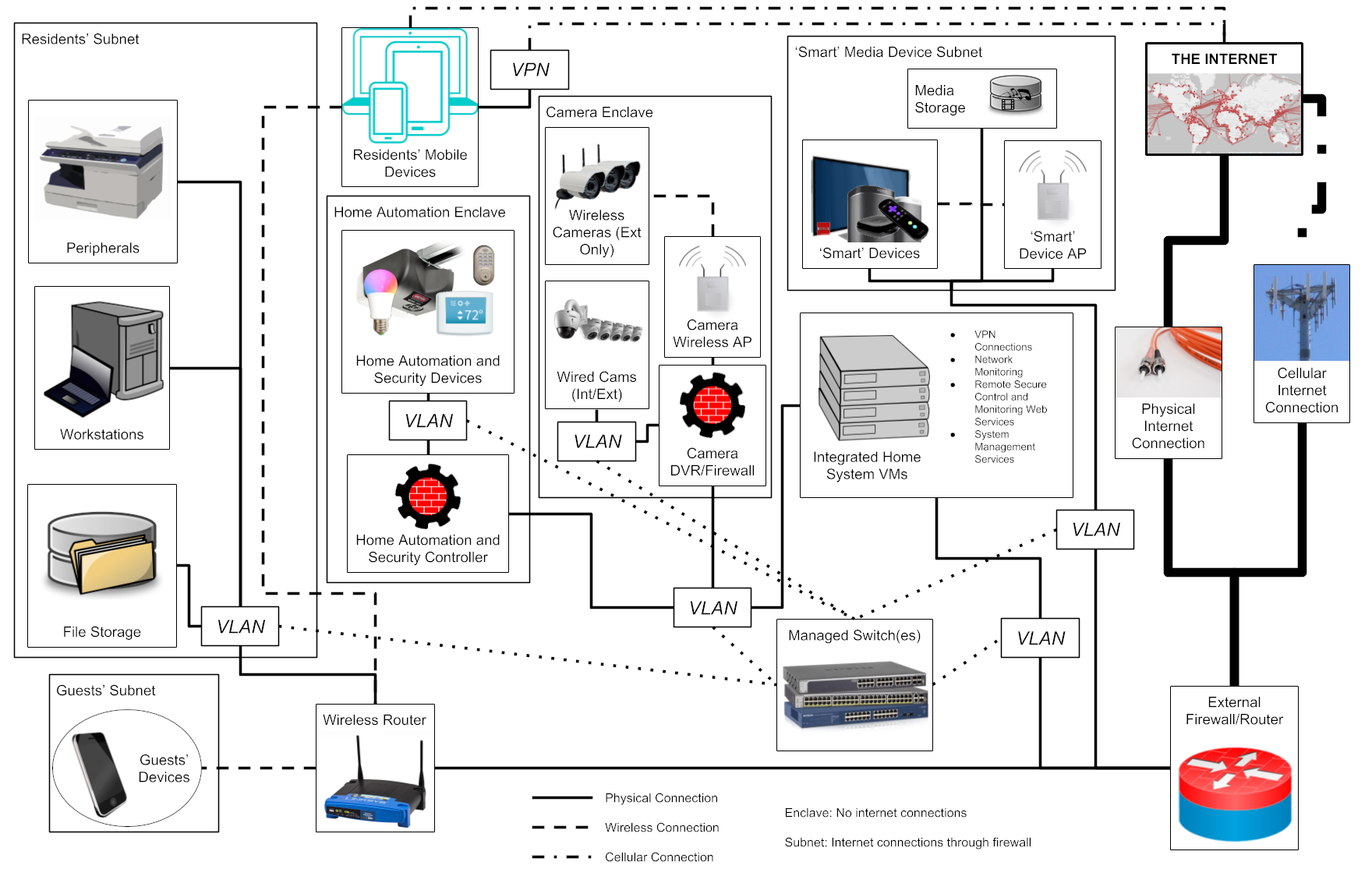
IHS is a framework that integrates a residence's security, automation and entertainment systems to provide enhanced responsiveness to occupants.
Purpose
IHS provides a single secure framework for the integration of personal computing devices, media devices and IOT devices.
- Coordinates the functionality of
- Home Security System
- Home Entertainment Systems
- Home Automation Systems
- Provides security in
- Cyber domain
- Physical domain
- Focuses on resposniveness to the needs and desires of the occupant.
Participants
- Occupants: Primary system users.
- Homeowners
- Decision makers and service consumers
- Other Residents
- Service consumers
- Guests
- Transient service consumers
- Homeowners
- Installers
- Owner needs consulting
- Chooses hardware
- Custom
- Off-The-Shelf
- Establishes framework
- Develop/select software
- Monitors
- Cyber specialists
- Monitor network and computer equipment
- Physical specialists
- Monitor physical security sensors
- Smoke/Water/Gas
- Intrusion detection
- Monitor physical security sensors
- Cyber specialists
Environment
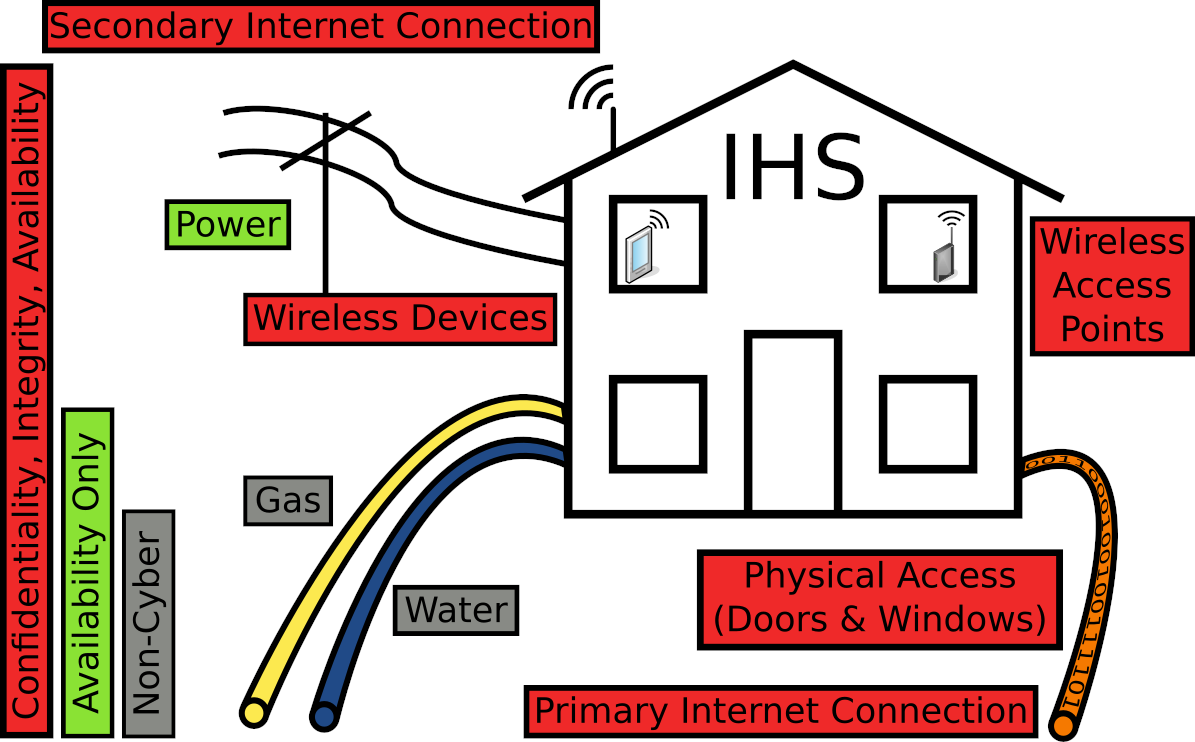
Residences face many security risks including various hazards and malicious actions.
- Hazards
- Fire
- Flood
- Gas leaks
- Excessive cold
- Malicious Actions
- Local threats
- Break-ins
- Package theft
- Vandalism
- Cyber threats
- Identity theft
- Privacy violation
- Ransomware
- Local threats
Policy Documents
- Mission Statement:
- Defines the goals and sets the scope for the system.
- Governance Policy:
- Defines the roles of everyone involved in system operation, and outlines the principals and procedures used to create operational procedures.
- Risk Management:
- Determines how risks and the effectiveness of mitigations are evaluated.
- Security Policy:
- Defines data and actions to be protected. Outlines who has control over data and who authorizes actions. Sets standards for enforcement.
- Design and operation informed by listed documents
Design Guidelines
- Network Security Design
- Secure Enclaves
- Verified Hardware
- Auditable software
- Zero Trust Architecture
- Multi-layer Mitigations
- Isolate untrusted devices
- Secure Enclaves
- Software Design and Deployment
- Custom software for integration
- Automation
- Endpoint security
- Third party monitoring
- Trusted software for common security techniques
- VPN
- Firewall
- IDS
- Data proteciton
- Custom software for integration
Operations: Staffing
Developing and maintaining any IT system requires continuous processes and a large workforce.
IHS spreads the required costs over many residents to provide the best value.
- Service personnel
- Customer Agents
- Network Monitoring
- IT Administration
- Process auditing
- Development
- Software engineers
- Programers
- Network architects
- Penetration testing
- Design auditing
- Overhead
- Business processes
- Overall auditing
Operations: Scheduling
- Patch cycle management
- Test and deploy within 1 week of release
- Cryptographic key management
- Annual rekeying of master certificates
- Training
- Monthly newsletters for users
- More detailed annual training seminar
- Testing
- Continous testing of new vulnerabilities
- Annual audits of security providers
- Quarterly Pen testing of model system
- Monthly agile software development cycle
Architecture

IHS is divided into a number of connected, protected enclaves.
- Enclave segregation
- Confidintiality
- Integrity
- Access Control
- Redundancy provides availability
- Electrical power
- Internet access
- Composition saves on cost
- Few switches
- Few fixed devices
- Virtual LANs
- Virtual Machines
Enclaves
- Internet
- Untrusted
- Source of many services
- Isolated using firewalls
- Black/White lists
- Behavior intelligence
- Infrastructure
- Managed Switches
- VM Hypervisors
- Virtual Machines
- Management
- Monitoring
- Uninteruptable Power Supply
- Web Surface
- Remote interface
- Monitoring
- Home automation control
- Interface with service providers
- Remote interface
- Resident’s Enclave
- Peripherals
- Printers, etc
- Filestorage
- Fixed workstations
- Mobile devices via VPN
- Peripherals
Enclaves Continued
- Camera Enclave
- Security Cameras
- Privacy concern
- Wired cameras preffered
- Wireless cameras
- External only
- Isolated on network
- Strict network filtering
- Guest Enclave
- Transient untrusted devices
- Access to internet only
- Smart Media Devices
- Smart TVs
- Other connected entertainment systems
- Home Systems Enclave
- IOT Devices
- Home automation section
- Home security section
- Limited computing power
- Interaction limited to specific VMs
Network Architecture
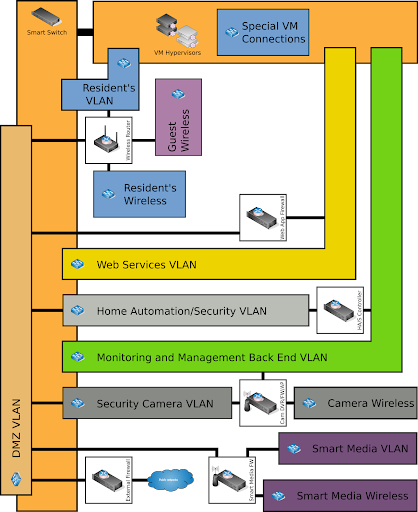
- Link Layer
- Inernal Ethernet
- External Ethernet
- Non-ethernet
- Internet Layer
- Endpoints
- Enclaves
- Proxies
- External Firewall/Router
- Transport Layer
- Internet zoning
- Dynamic port security
- VPN
- Application Layer
- Trust isolation
Cybersecurity Tools
- Security Models
- Lattice Model
- Information Flow Model
- Clark-Wilson Model
- Use and Abuse Cases
- Behavioral modelling
- Virtualization
- Isolates sensitive tasks
- Virtual Private Networking
- Mobile Devices
- Remote access
- Cryptography
- Enrypt sensitive data
- In transit
- At rest
- Access control
- PKI Infrastructure
- Enrypt sensitive data
- Authentication
- Multifactor authentication
- Level depends on enclave
- Access Control
- Role based
- Session management
Integraged Piloting and Avionics Architecture
Collaborative General Aviation Avionics
Conceptual enterprise and reference model design for future collaborative avionics architecture of General Aviation aircraft.
Overview
The IPAA concept proposes a development program for the avionics suites in General Aviation Aircraft.
- Features:
- Collaborative
- Agile
- Model Based
- Interoperable Components
- Open Architecture
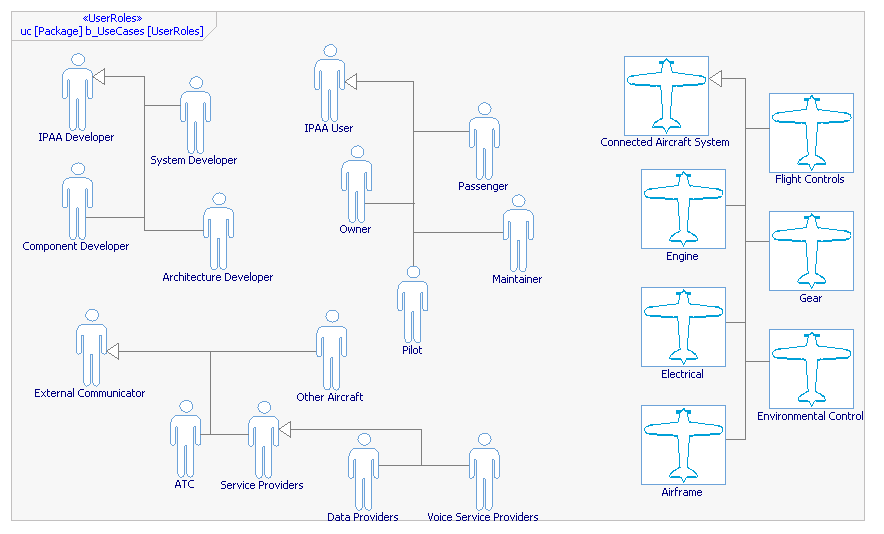
Participants
Split by stakeholder group
- Consumers - Pilots and aircraft owners/operators.
- Integrators - Aircraft manufacturers, panel specialists, and amature builders.
- Component Developers - Established and start-up designers, manufacturers and software publishers with products relevant to GA flight.
- Regulators - National and international airspace owners and regulators with jurisdiction over the safe operation of GA aircraft.
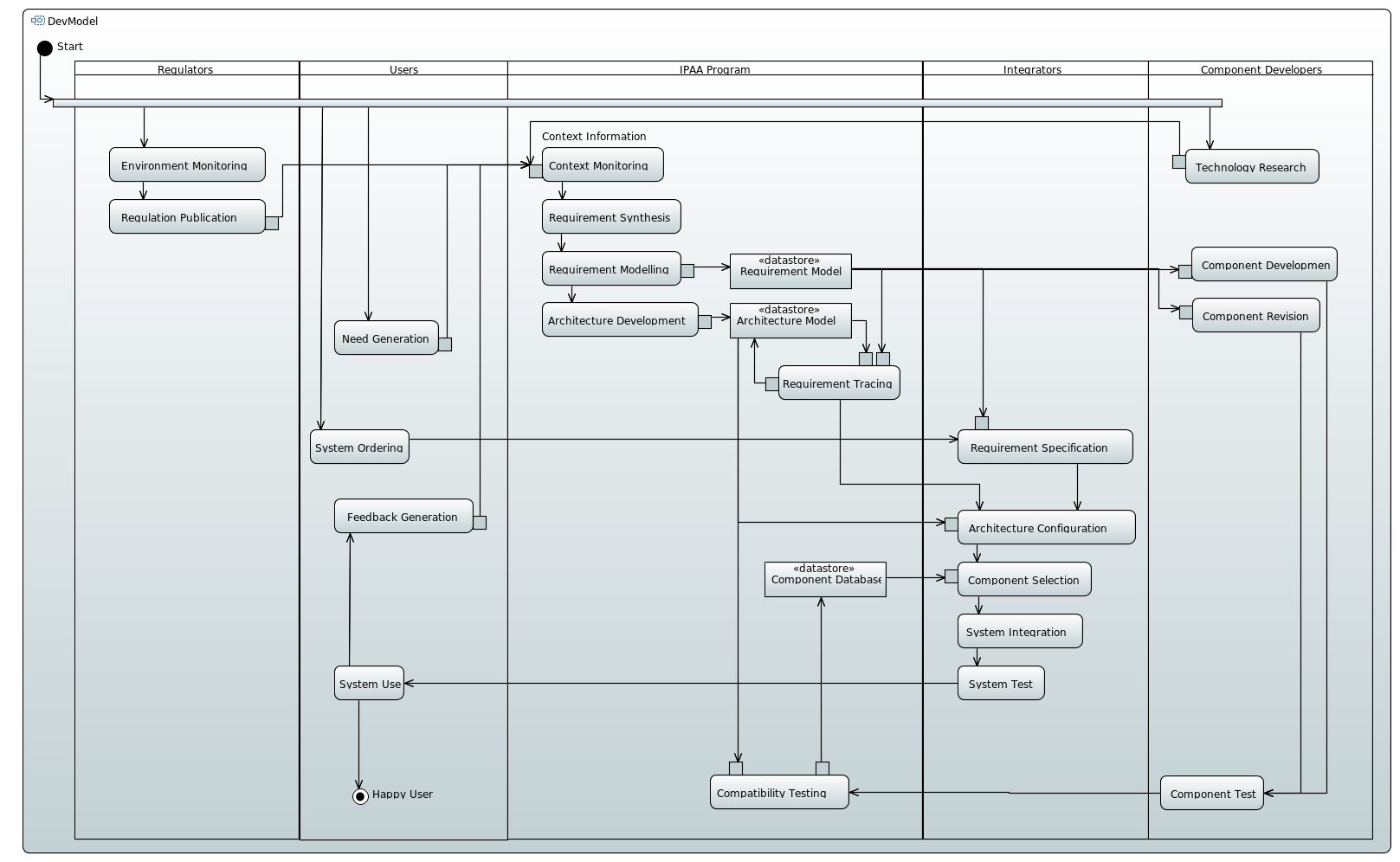
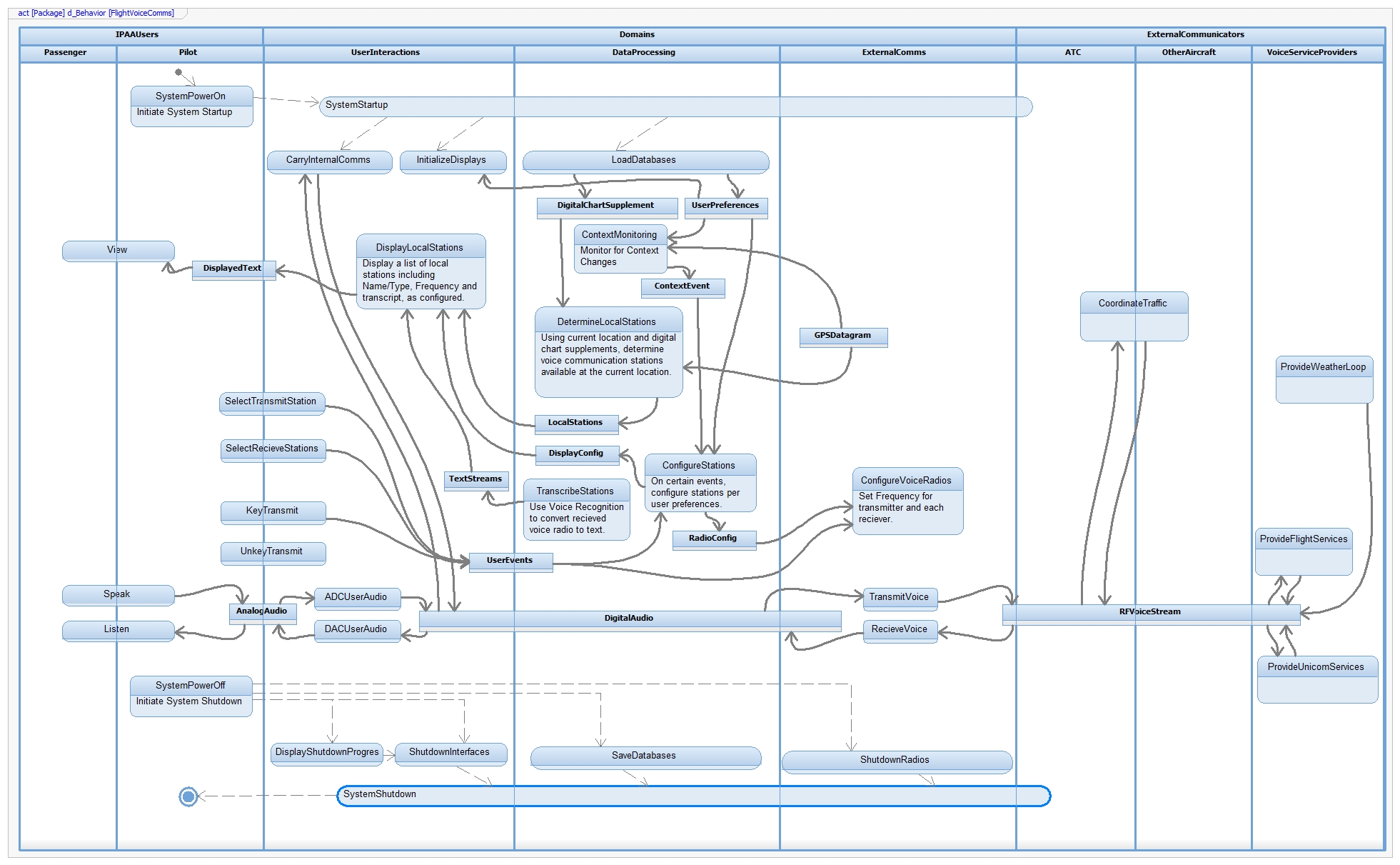
Development Model

Activity diagram of the IPAA development model.
Development Model
Model Based Systems Engineering
- Reference model used throughout development process
- Interfaces clearly defined to ensure interoperability
- Reuse of engineering work across enterprise
- Reduced cost of custom implementations using common components
Agile Development
- Parallel iterative designs at all levels
- Responsive to changing markets and needs
- Incorporate stakeholder feedback in useful timeframes
Enterprise Organization
Tier 1
- Worldwide Governance Board - Overarching policy decisions.
- ICAO, IAOPA, EAA, GAMA
- Stakeholder representatives from regional boards
- Executive Organization - Leadership and guidance for day to day operations.
- CEO, COO, CIO, CFO, etc
Enterprise Organization
Tier 2
- Policy
- Regional Governance Boards - Regional policy inputs to worldwide board.
- Stakeholder Groups - Body of interested stakeholders, separated by type.
- Operational
- Initiative Coordination Office - Manages development process.
- Information Office - Handles information policy and inforcement.
- Financial Office - Manages flow of money.
Enterprise Organization
Tier 3
- Working groups - Project teams working on a specific set of issues.
- Test Labs - Provide independent tests of IPAA components.
- Unified Support team - Customer service and technical support for IPAA systems.
- Administrative Departments - Accounting, HR, IT, etc.
Enterprise Governance Policy Documents
- Development Policy
- Program Management Plan
- Systems Engineering Master Plan
- Risk Management Plan
- Information Policy
- Ethics Standards
- Information Security Process
- Publication Guidelines
- Legal Policy
- Training Program
- Membership Policy
- Administrative Policy
Enterprise Governance Processes
- Executive Organization makes day to day decisions with oversight of Worldwide Board.
-
Regional boards research and make recommendations on regional issues.
-
Decisions made at tier level as determined by policy documents
-
Metrics and processes drive action.
Requirements
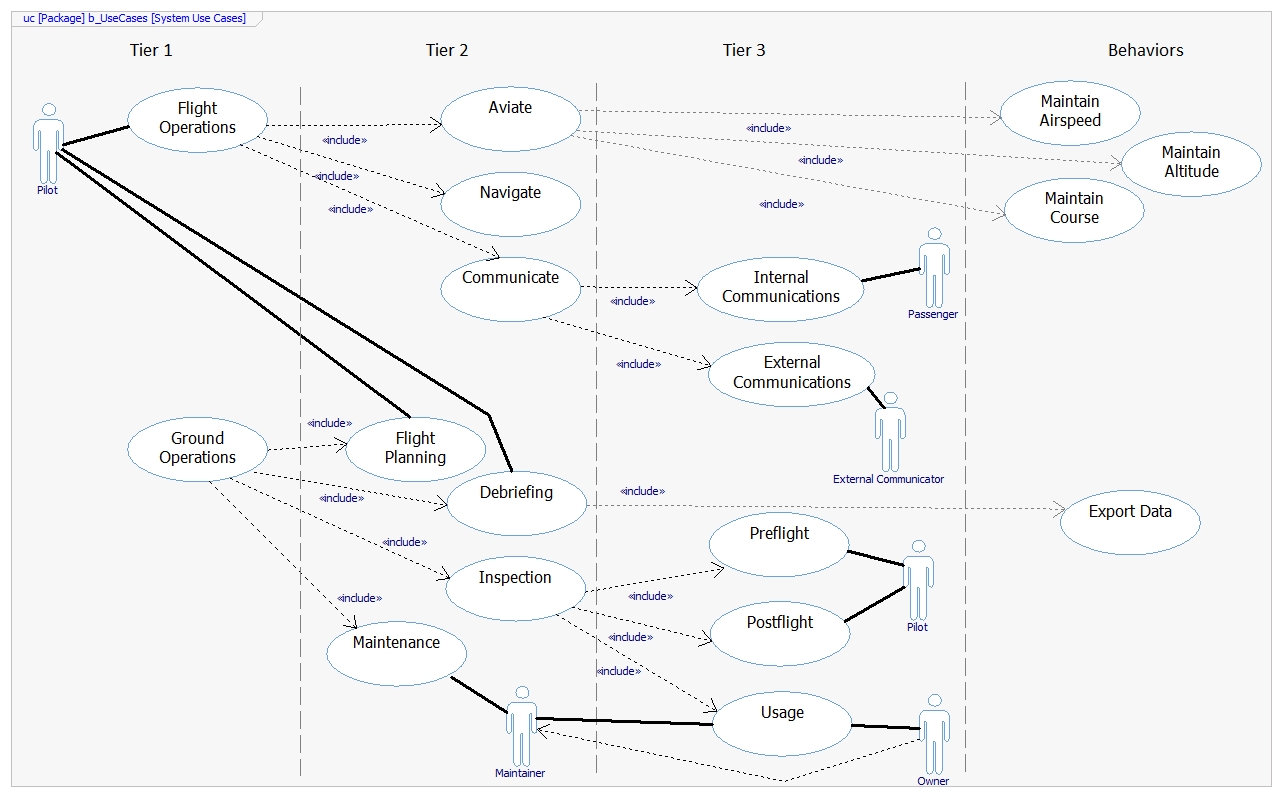
- Requirements Engineering Activities
- Context Monitoring
- Requirement Synthesis
- Requirement Modelling
- Requirement Tracing
- Requirements Model
- Parameterized requirements and relations
- Modelled behaviors
- Generalized for all possible systems
- Customized for implementation
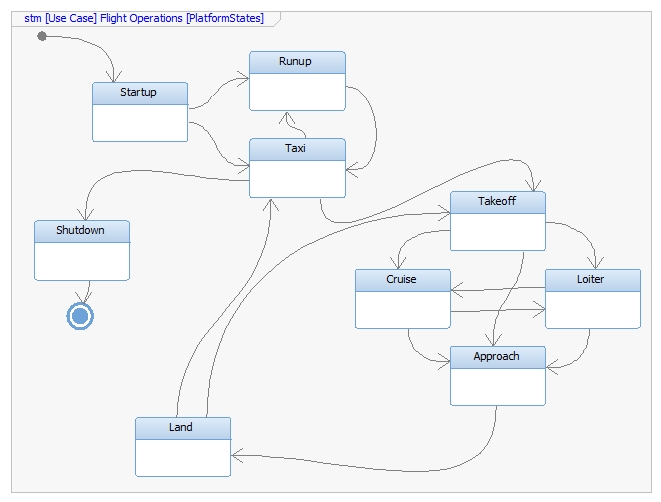
Architecture
- Open Systems Architecture
- Loose Coupling
- Manufacturer Interoperability
- Open Data Environment
- Service Orientation
- Hardware, software and external interactions abstracted as services
- Reference Architecture
- Generalized for all possible systems
- Customized for implementation
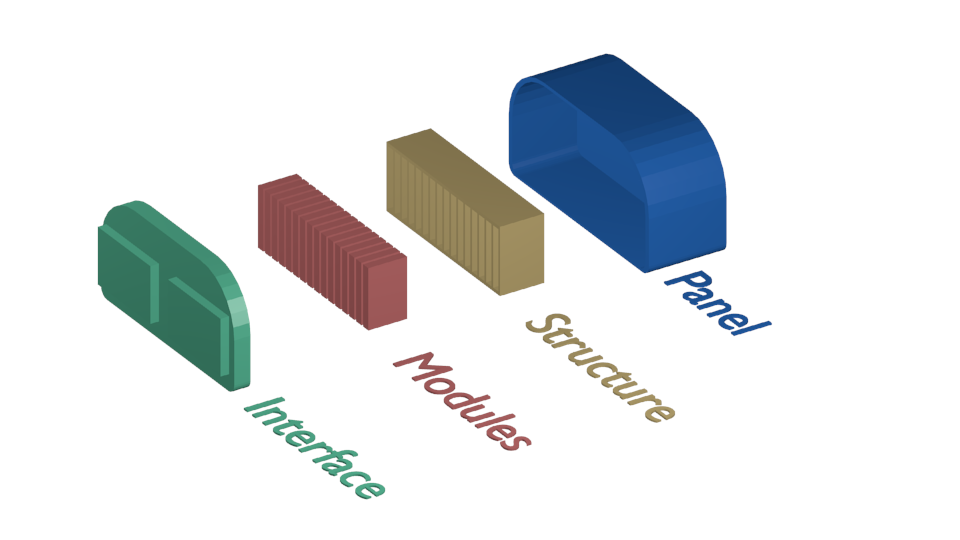
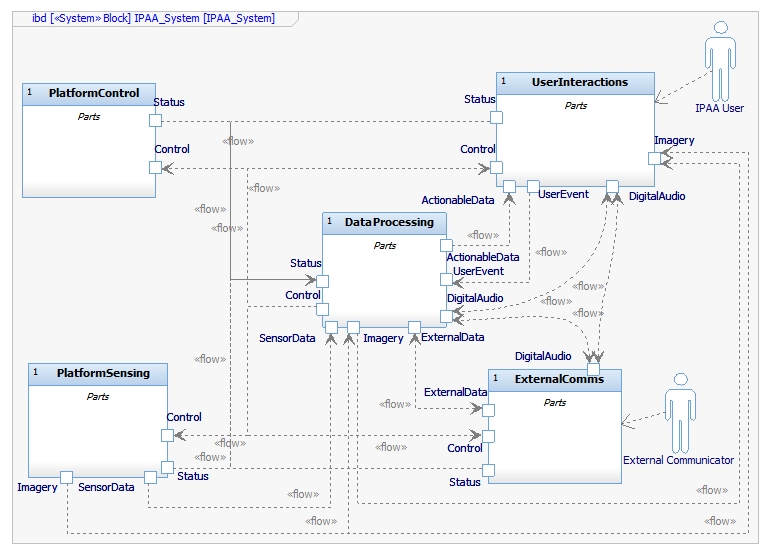
Architecture Services
- High level services
- Interact with users
- Interact with external entities
- Rely on lower level services
- Lower level services
- Bundles of functionality
- Rely on resources
- Resources
- Finate quantity
- Allocated carefully
Architecture Services
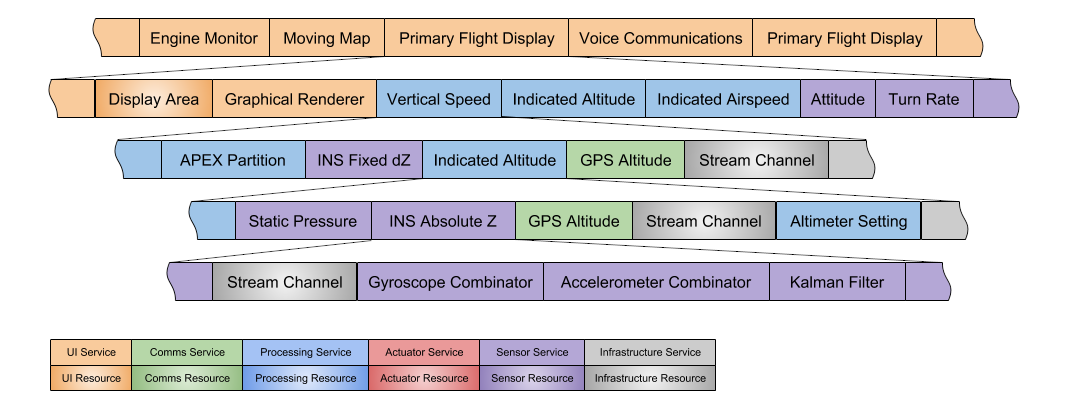
Example of how high level services are composed from low level services and resources.
System Security
System security a safety concern.
Cyber security, physical security and privacy considered from the ground up.
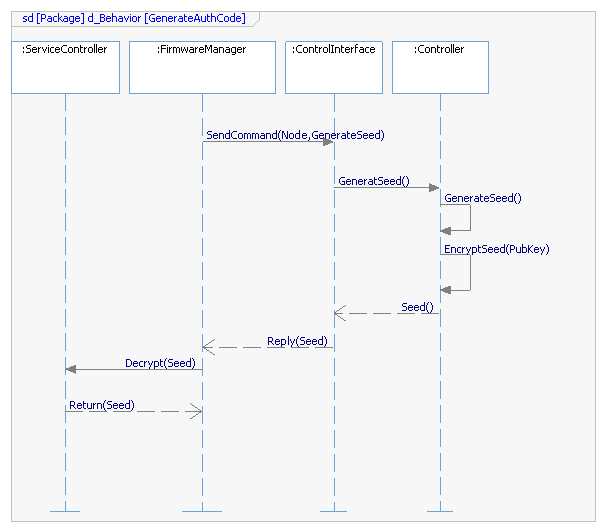
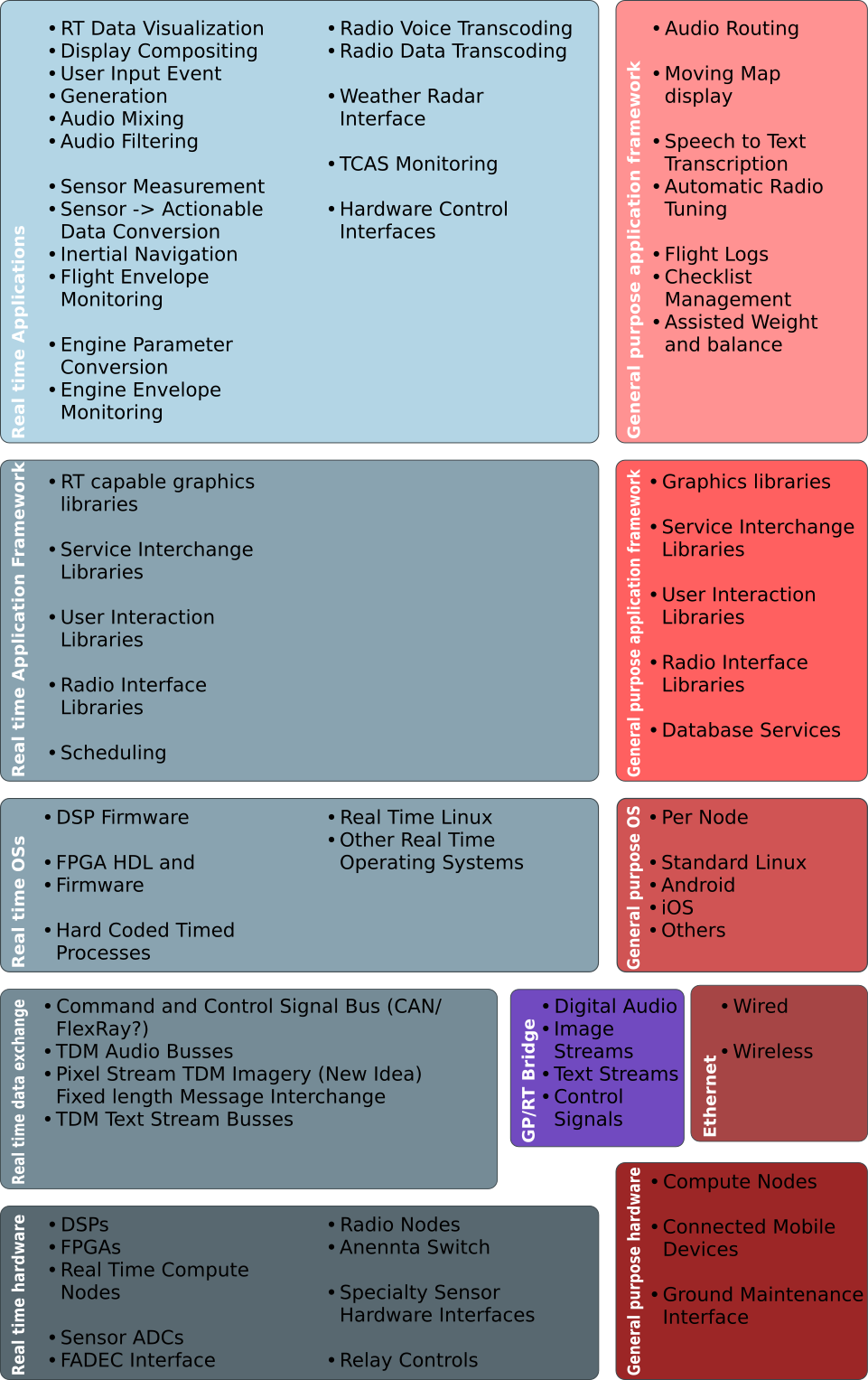
System Implementation
Component Development
- Implements IPAA requirements
- Conforms to IPAA reference architecture
- Conducted by Component Manufacturers
- Tested by IPAA program labs
System Implementation

System Integration
- Requirements customized for application
- Architecture configured based on requirements
- Components selected based on implemented requirements and architecture
- System built and tested.
System Implementation
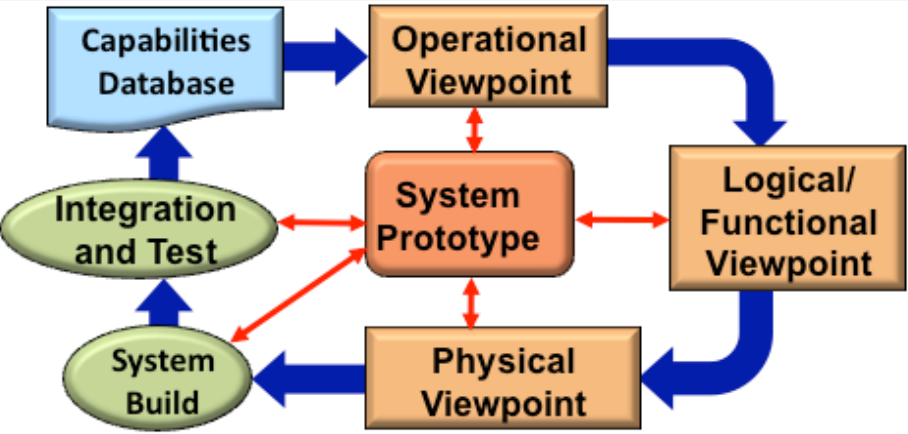
MBSAP courtesy Dr. J.M. Borky
Operations and support
- Pilots and owners use system and seek support if needed.
- Unified Support Team provides support and technical guidance
Product End of Life
- Some components can be recertified and reused
- Safe disposal of all components planned for.
Completing the Loop
- Unified Support Team provides feedback to requirements and architecture.
- Pilot feedback actively sought.
Cyber-Physical Systems
Mechanics + Sensors + Electronics + Software
ADSBSee
The Automated Plane Spotter

A cyber-physical system, ADSBSee automatically takes pictures of aircraft in the sky overhead.
Detection

The ADSBSee station detects the transponder signals of nearby aircraft and uses this to determine each aircraft’s relative direction.
Tracking
Stepper motors controlled by a PocketBeagle Single Board Computer (SBC) point the telescope at the aircraft.
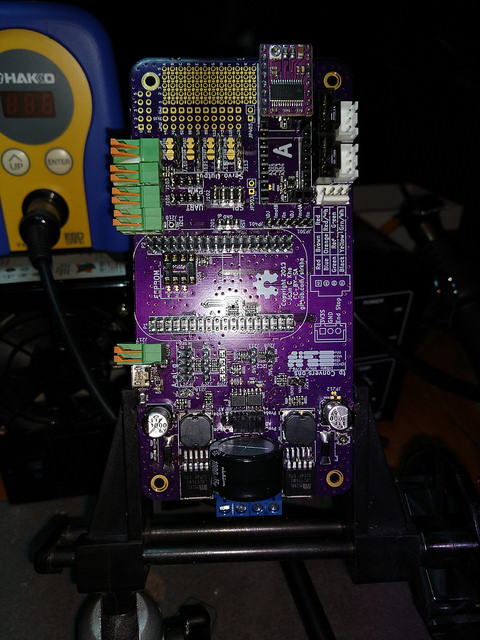
Image Capture
A digital camera captures images or video of the aircraft through the main telescope.
Two smaller telescopes provide a stereographic display via Raspbery Pi Cameras.

Distributed Computing

One Raspberry Pi SBC recieves and processes the transponder signals, determines the stations position via GPS, senses the orientation, and provides WiFi access to the station
Distributed Computing

The other Raspberry Pi directs the automation of the station, processes captured images and provides a web based user interface.
Distributed Computing

The PocketBeagle provides a REST interface that controls the station’s motion.
Real-time microcontrollers built into this SBC ensure that the station’s motion aligns with its target at the right time.
System Architecture
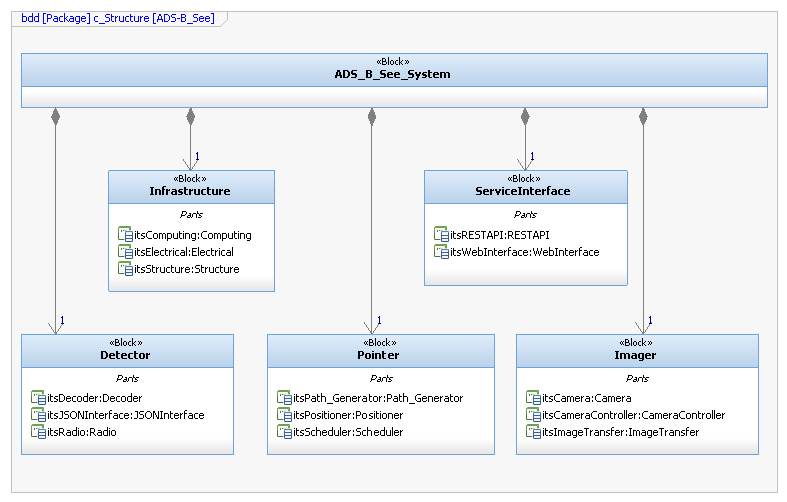
Block diagram of the ADSBSee system
System Architecture
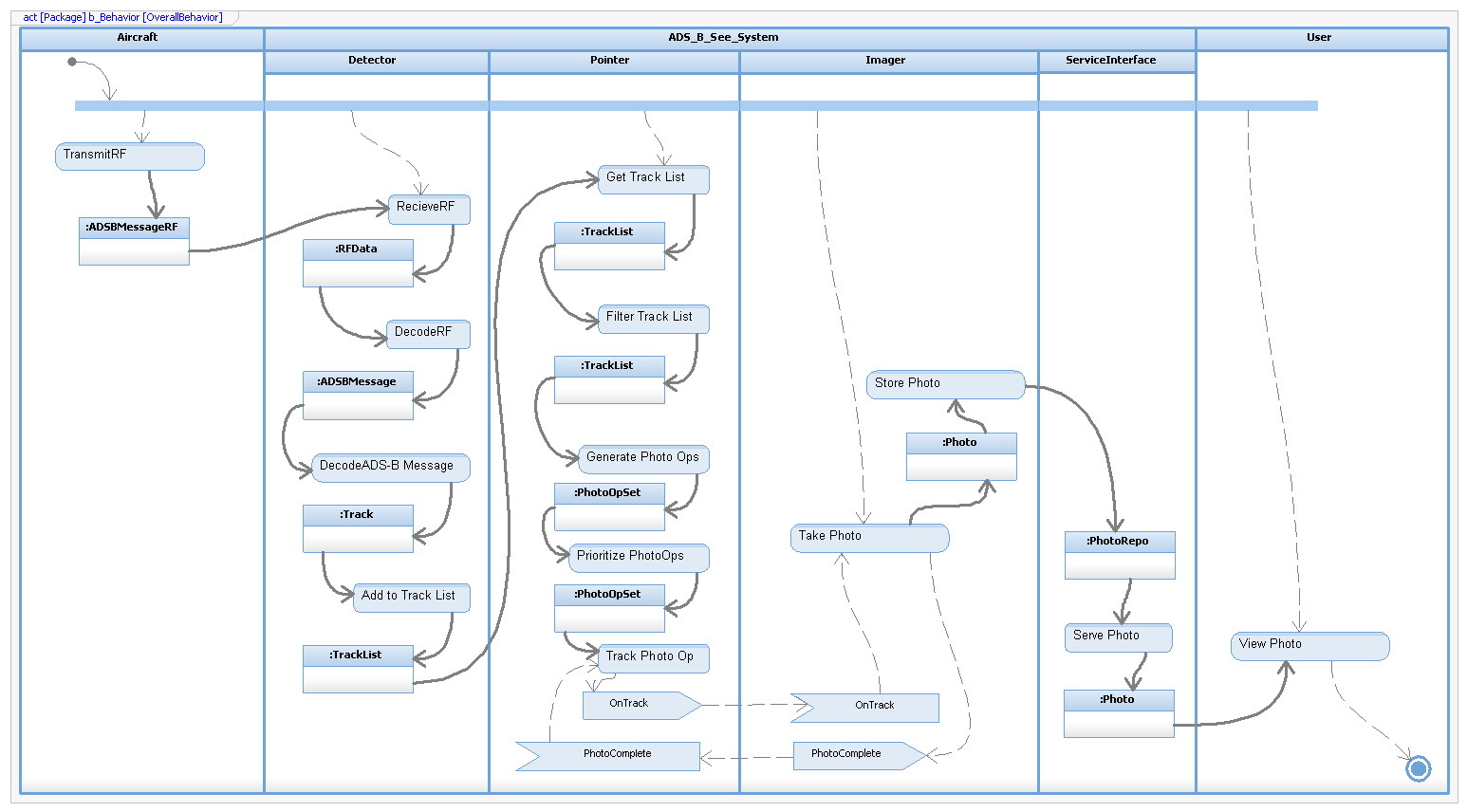
ADSBSee activity diagram
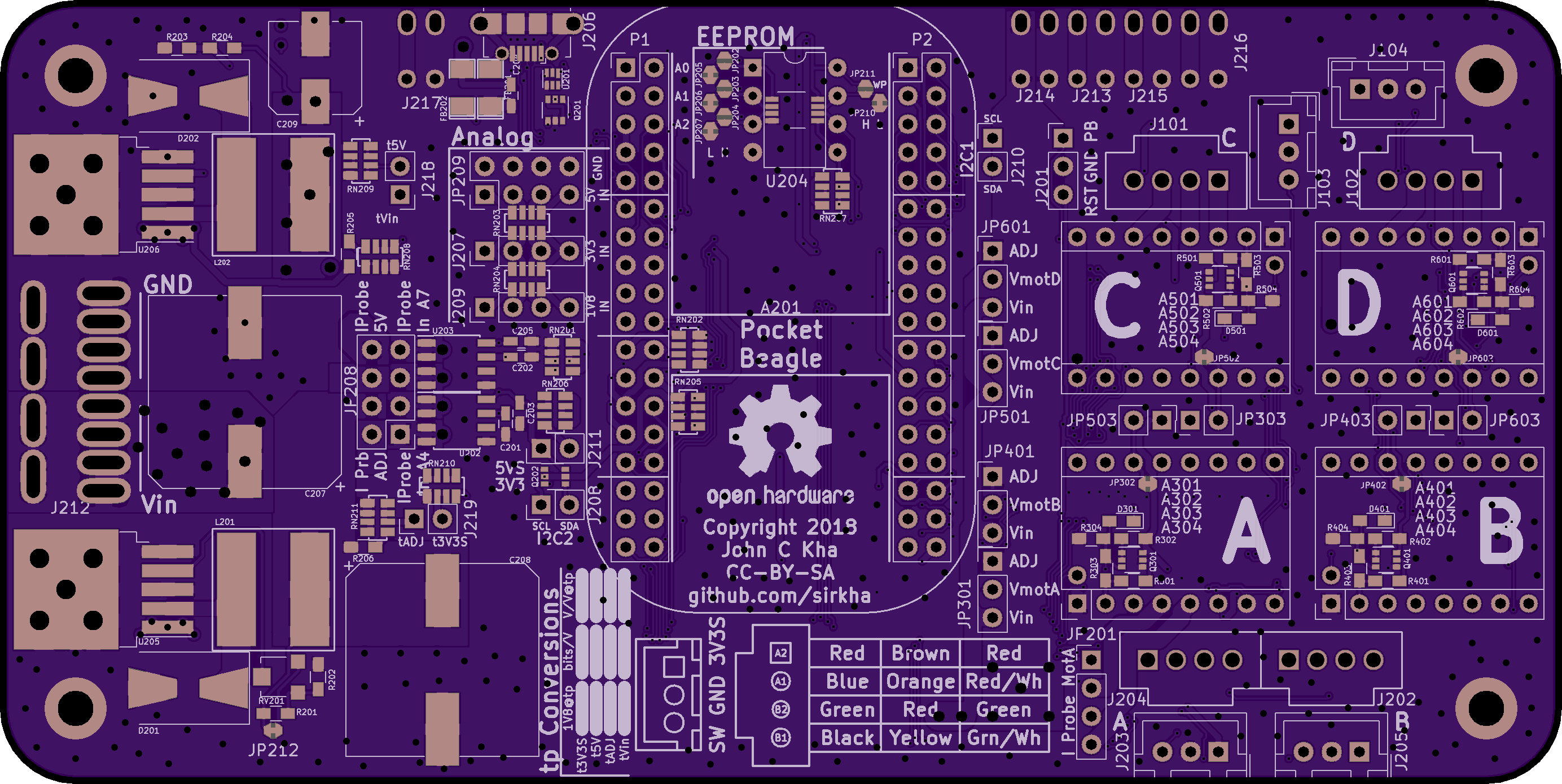
Pocket Beagle Stepper Carrier
Real time control for robotics projects.
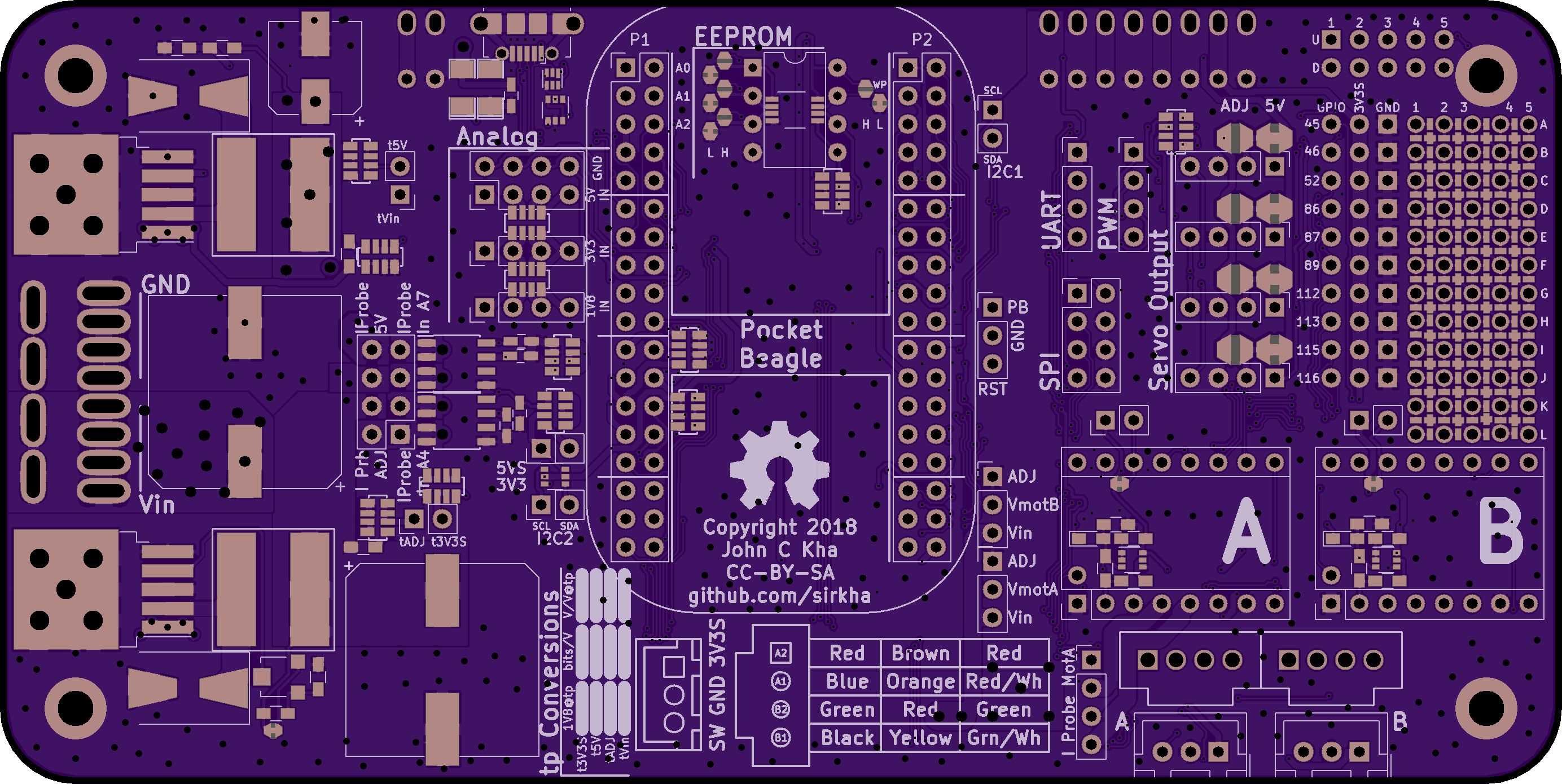
Backplane board and power supplyconnecting a PocketBeagle Single Board Computer to Pololu stepper motor drivers.
Overview

- Tiny single board computer
- Real time capabilities
- Large I/O header
- Multiple driver chips
- Mostly pin-compatible form factor
Dual and Quad Versions
- Quad version holds 4 stepper-drivers to drive 4 stepper-motors
- Dual version replaces two stepper-drivers with
- Combination of 4 PWM or Servo channels
- SPI, UART Comms
- Prototyping Area
- GPIO

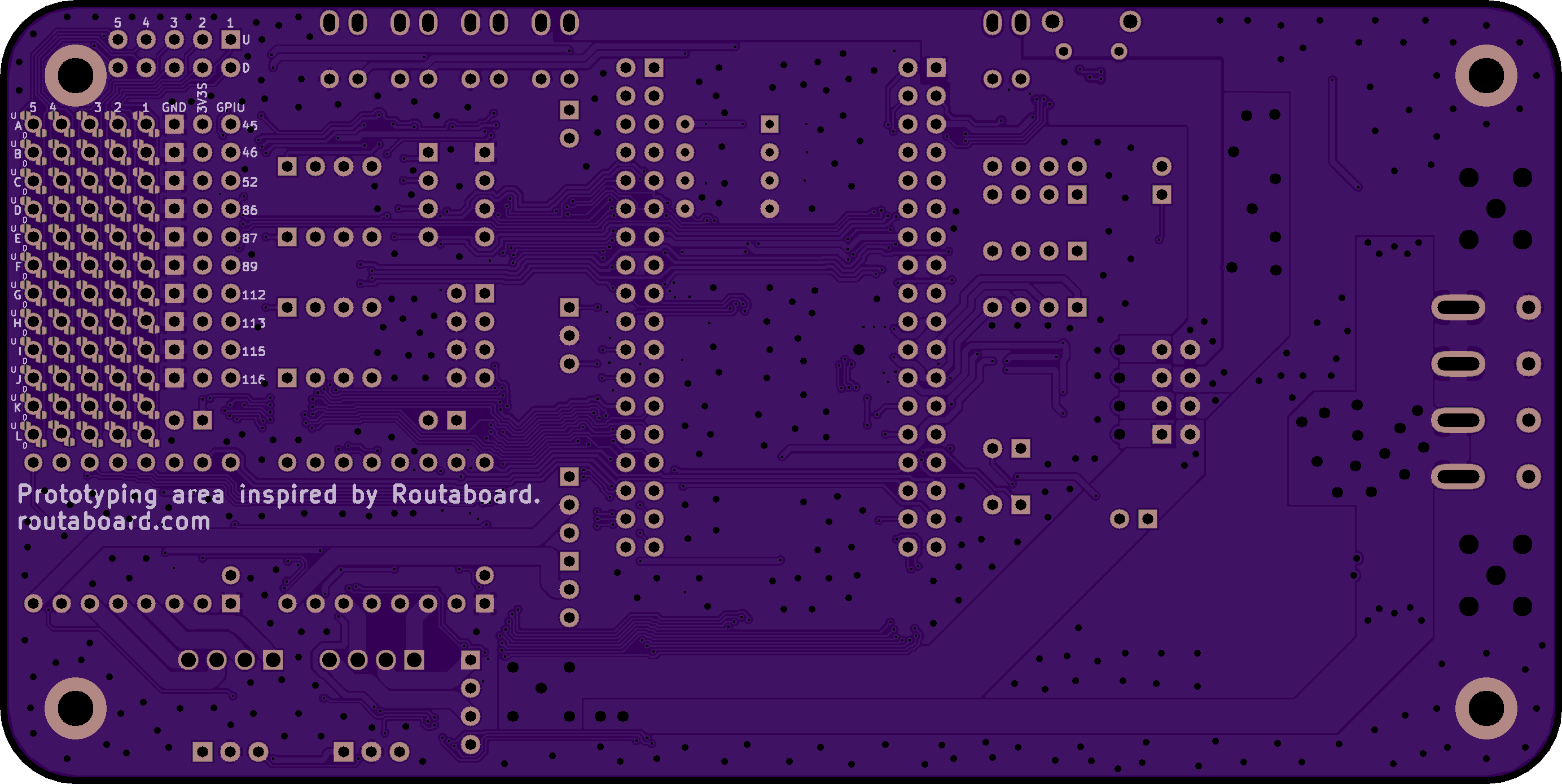
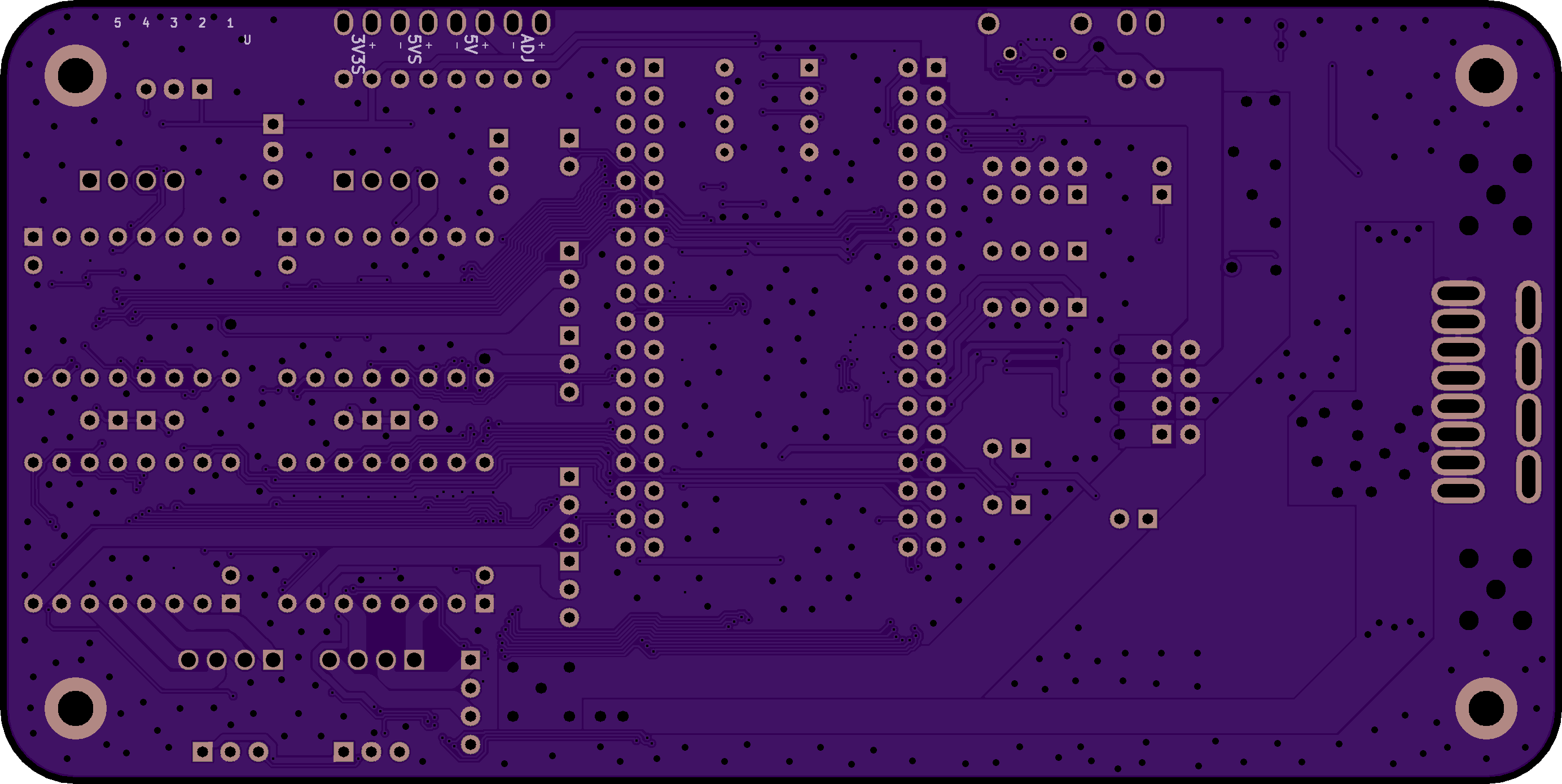
PBSC Hardware Features
- Dedicated 5V power supply
- Adjustable power supply for motors or other
- Measurement capabilities
- Voltage on both power supplies
- Voltage on PocketBeagle rails
- Jumper configurable current measurements
- High configurability
- Software control of stepper-driver parameters
- Jumper configurable options for powering stepper-drivers
- Stepper current limit set using on board measurement
- All power rails accessible with screw in terminal blocks
- Breaks out communication capabilities
- I2C, SPI (Dual Only), UART (Dual Only)
Software Features
Work in Progress
- Broad real time capabilities
- Controlled step rate
- Controlled acceleration curve
- Table of times to step at
- PID controls
- Accessible API
- Abstract real time functionality to non-real time systems
- Simplify motion programing with abstract concepts
- Track path
- Goto point as quickly as possible
Isolated Power Line Data Transmission
Modelling, Simulation and experimentation
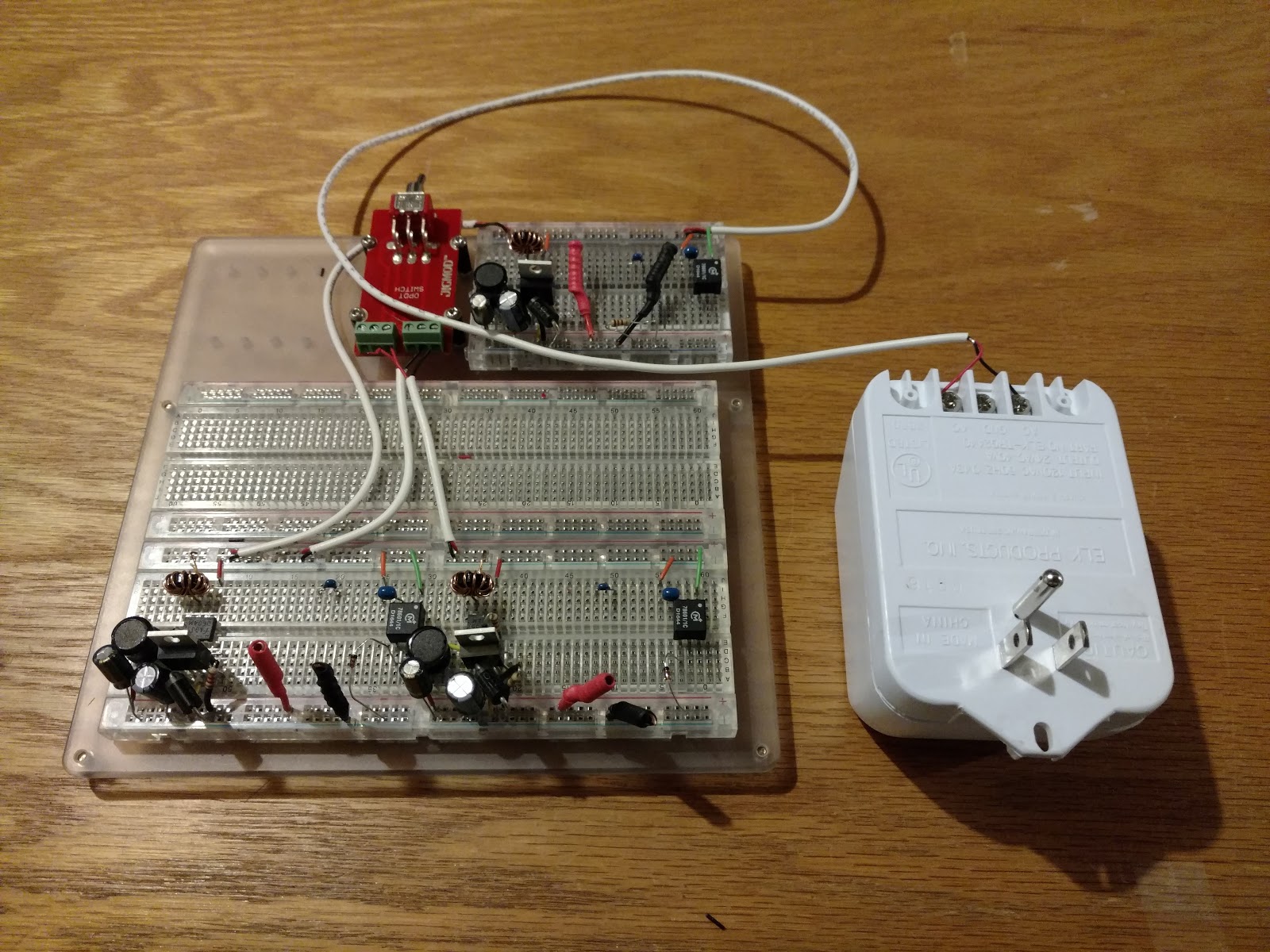
Transmission of data over a 24VAC power line.
MECH-513 Project
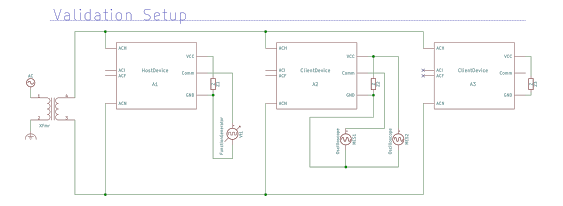

Modelling and simulation of a system designed to transmit data over 24VAC power lines used to power devices such as thermostats.
Setup
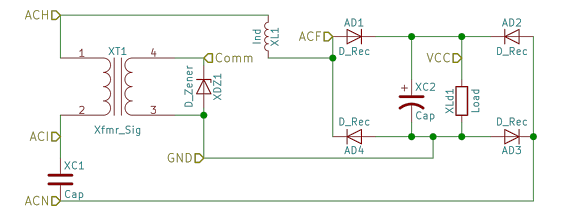
Each tranciever is modeled in ngspice and simulated as part of the system.
Spice Circuit
.subckt device ACH ACN Comm VCC GND
+ C1_val=1u C1_esr=0
+ L1_val=1mH L1_cself=1pF L1_rdc=100m
+ C2_val=100u C2_esr=1m
+ XT1_l=2000u XT1_r=.13 T1_cs XT1_ciw=22pf XT1_rcl=10M
XDZ1 GND Comm D_Zener
XT1 ACH ACI Comm GND Xfmr
+ L_P={XT1_l} L_S={XT1_l} N_P=1 N_S=1.001
+ R_P={XT1_r} R_S={XT1_r}
+ C_P={XT1_cs} C_S={XT1_cs} C_IW={XT1_ciw}
+ R_CL={XT1_rcl}
XC1 ACI ACN Cap
+ cval={C1_val} lser=0
+ rser={C1_esr} rleak=10M
XL1 ACH ACF Ind
+ lval={L1_val} cself={L1_cself}
+rdc={L1_rdc} rac=10G
D1 ACF VCC D_Rec
D2 ACN VCC D_Rec
D3 GND ACN D_Rec
D4 GND ACF D_Rec
XC2 VCC GND Cap
+ cval={C2_val} lser=0
+ rser={C2_esr} rleak=10M
.ends device
Component Modelling
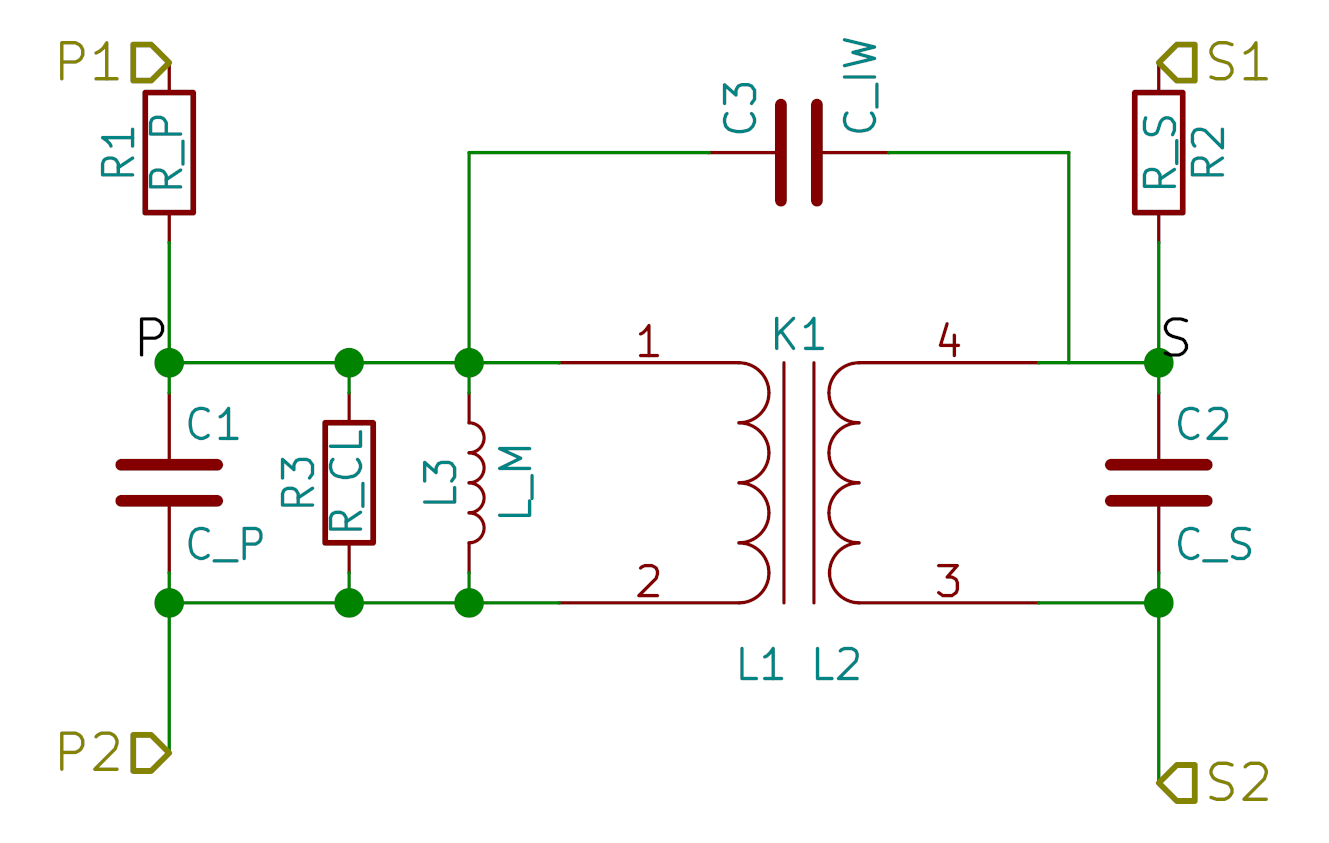
This transformer model demonstrates how components of the device are also modelled.
Spice Circuit
.subckt Xfmr P1 P2 S1 S2
+ L_P=1m L_S=1m N_P=1 N_S=1
+ R_P=100m R_S=100m
+ C_P=0 C_S=0 C_IW=100p
+ L_M=100n R_CL=1G
L1 P P2 {L_P}
L2 S S2 {L_S}
K L1 L2 {N_P/N_S}
R1 P1 P {R_P}
R2 S1 S {R_S}
C1 P P2 {C_P}
C2 S S2 {C_S}
L3 P P2 {L_M}
C3 P S {C_IW}
.ends Xfmr_Sig
Component Simulation
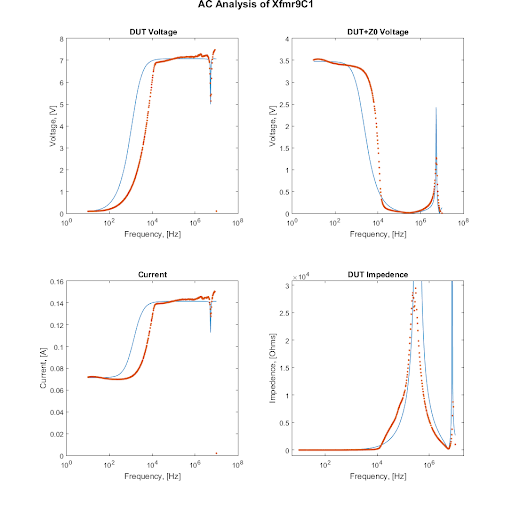
The model is then run in the ngspice simulator and the resulting response is compared with the response of a real transformer with the same parameters to verify the device models.
System Simulation Verification Failure
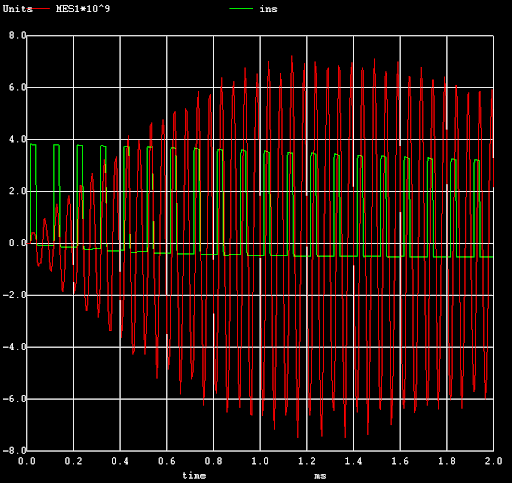
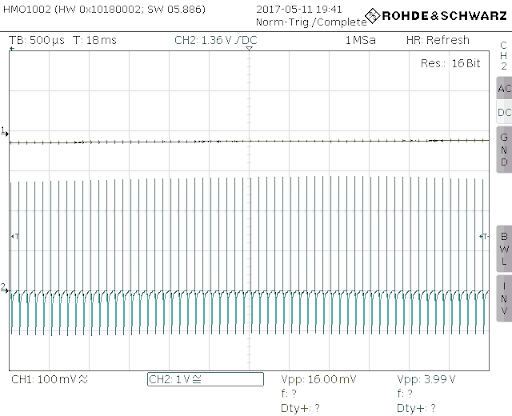
Unfortunately, ngspice limitations prevent accurate modelling of the system as a whole, leading to a failure to validate the overall model.
Miscellaneous
Miscellaneous small projects.
3D Printing
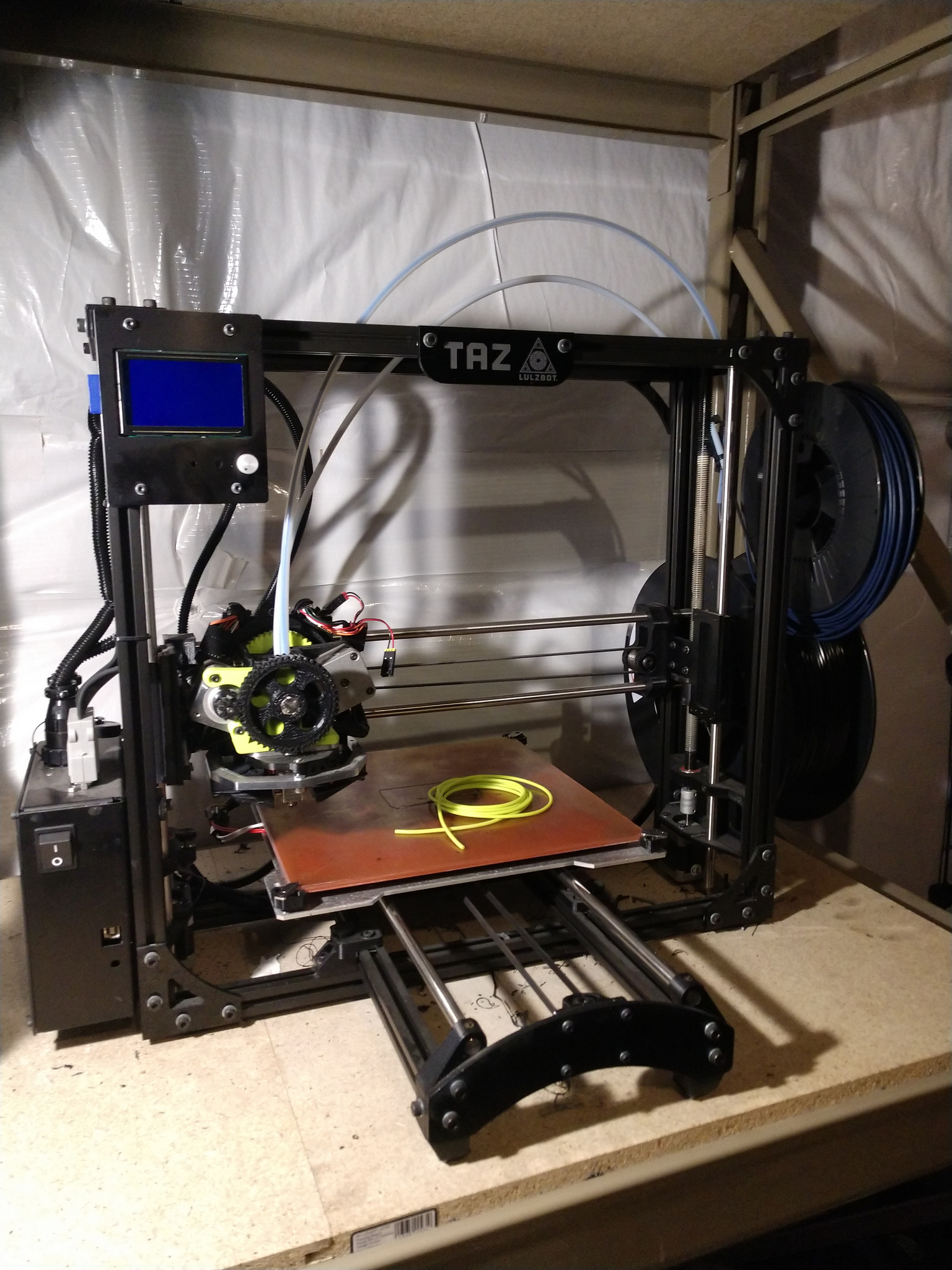
FDM Printing on my Lulzbot Taz 5
3D printing since September 2014

- Lulzbot TAZ 5
- Thermoplastic Fused Deposition
- Dual extruders
- Designs in:
- Blender
- Solidworks
- OpenSCAD
- Slicing in
- Slic3r
- Cura
- Dual extrusion
- ABS, NinjaFlex, Nylon, PLA, HIPS
Tripod Bracing

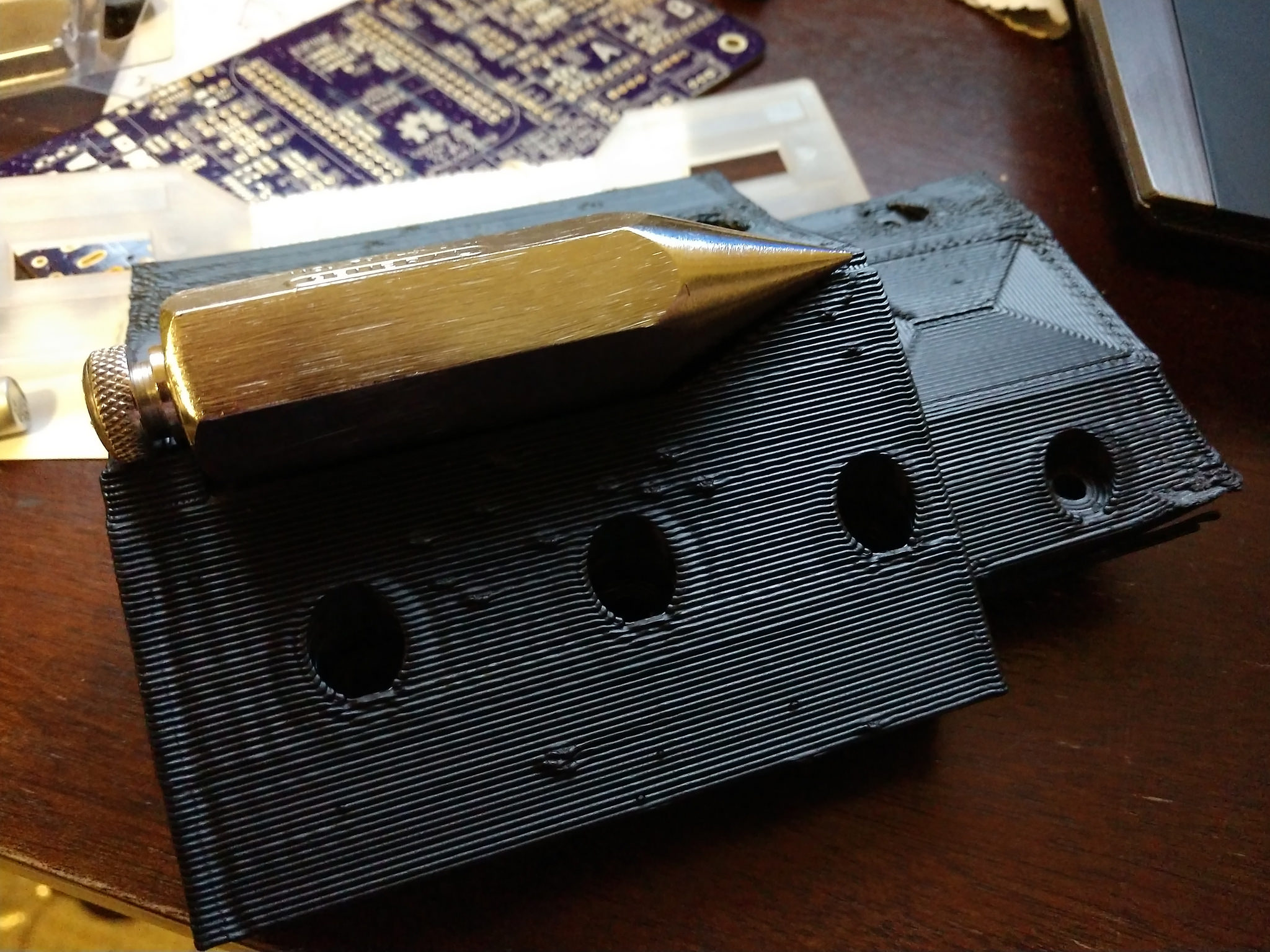

This multi piece printed tripod leg bracing attaches to a surveying tripod. When folded, it encases a hexagonal plumb bob. When deployed the center platform is used with the plumb bob to level the tripod.
Tripod Bracing

Mechanical design of hinges
- Arms are printed so forces from the rod are distributed over the print layers instead of being focused between them.
- Reinforcement on the platform and leg attachments are acetone welded on for the same purpose.
Sample Holder

Sample holder for disc-shaped geological samples.
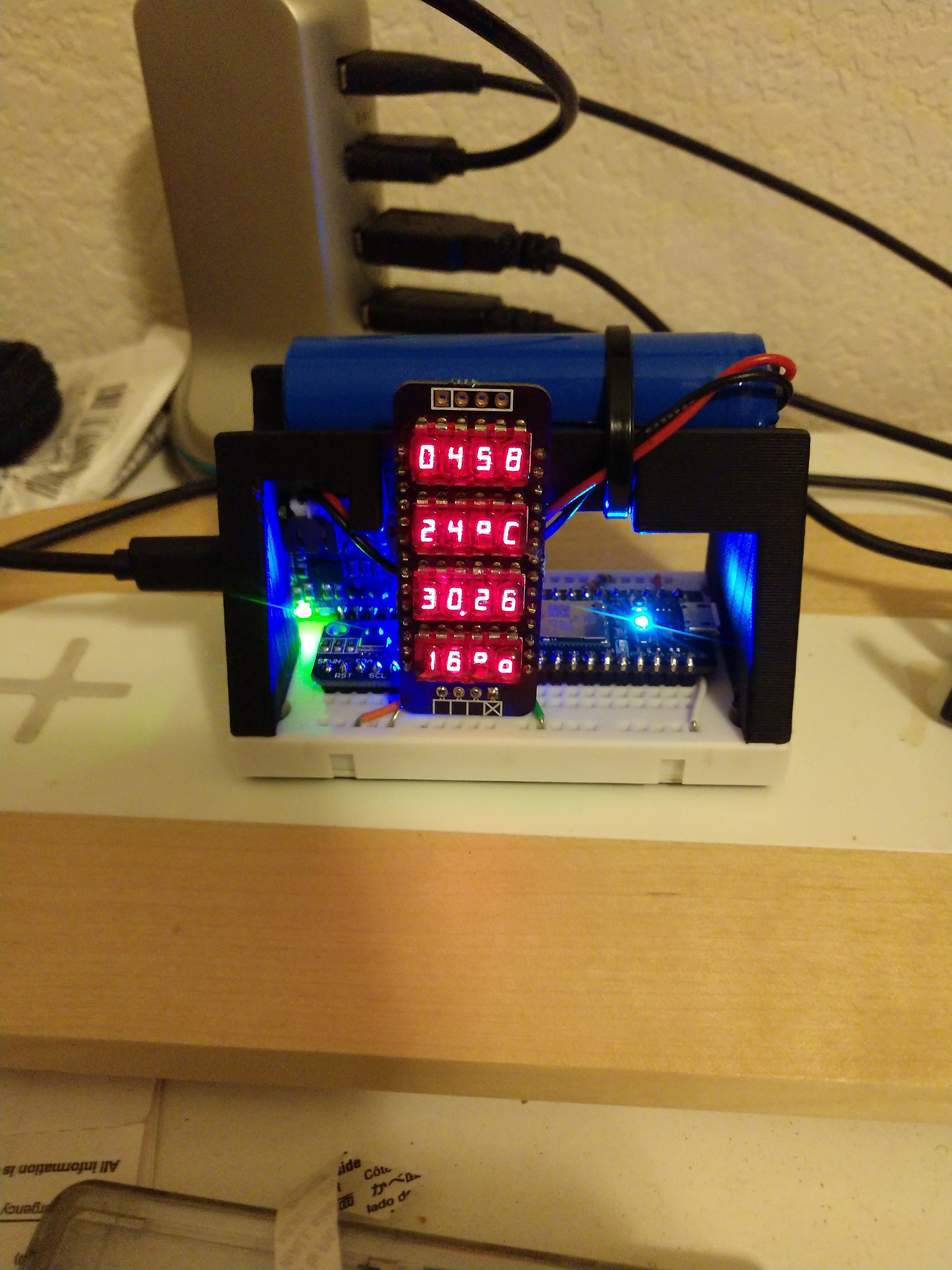
Battery Holder
Battery holder for air quality and clock display.
The 3D printed part fits into an existing breadboard.
FlexyDualy Dual Print Head


3D printing 3D printer parts. FlexyDualy v1 print head from Lulzbot in HIPS.
Space Mouse Mount


Added a place to mount a space mouse to a regular office chair.
Exacto Knife Cap

Exacto knife didn’t come with a cap. Not a problem. Clear NinjaFlex can help.
Other Technologies
In addition to hands on experience with Thermoplastic FDM printers, I keep up with other additive manufacturing technologies.
- Resin-curing
- Stereolithography (SLA)
- Direct Light Processing (DLP)
- Metalic FDM
- Automated MIG
- Binder printing
- Metals, Ceramics
- Sintering
- Powder Bed
- Selective Laser-sintering
- Selective melting
My B.S. in Metallurgy and Materials Engineering helps give me an advance perspective in the production of 3D printed parts using any technology.
CAD Application Experience
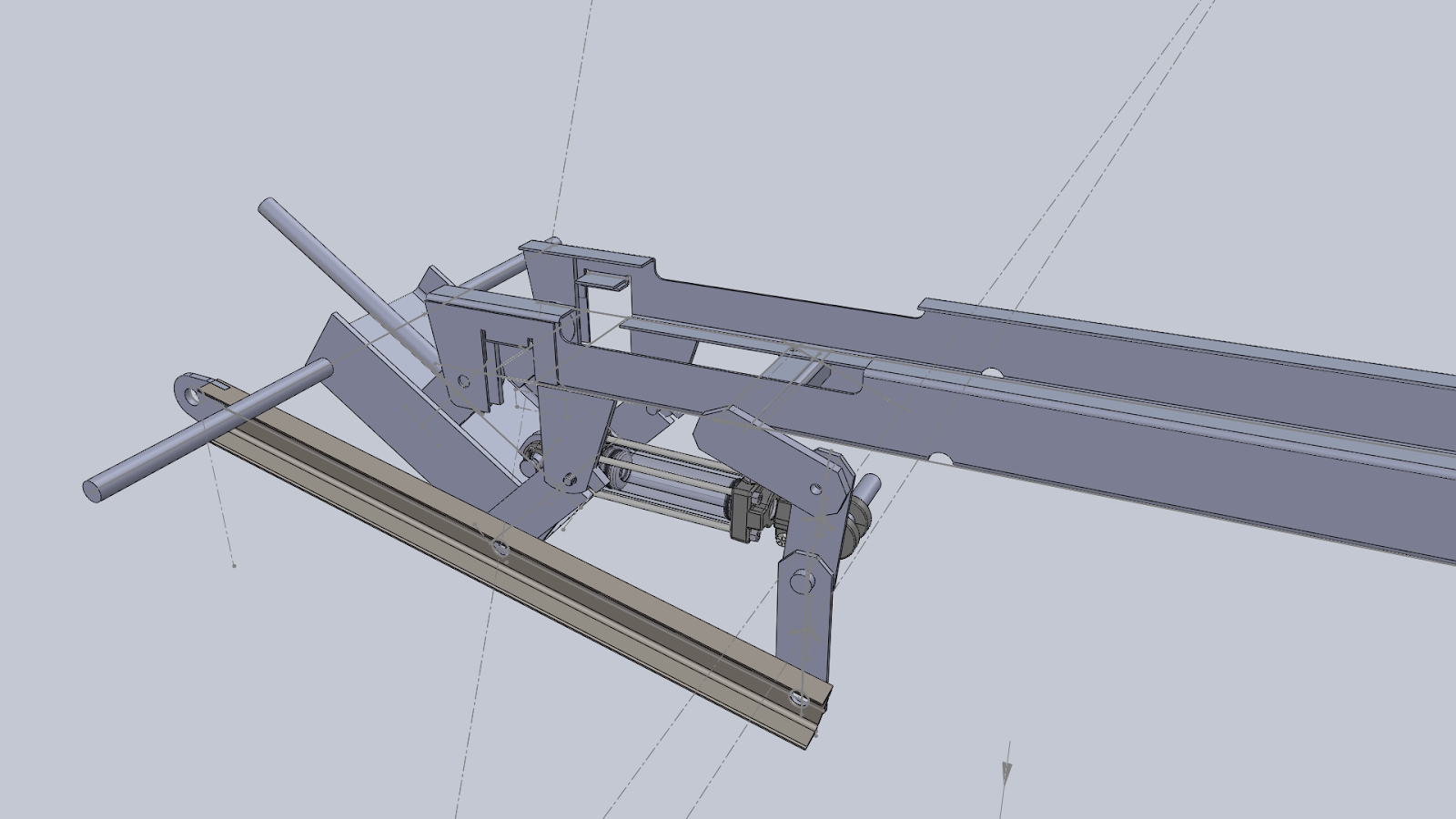
Examples of CAD work for various minor projects
IBM Rational Rhapsody (SysML/UML)
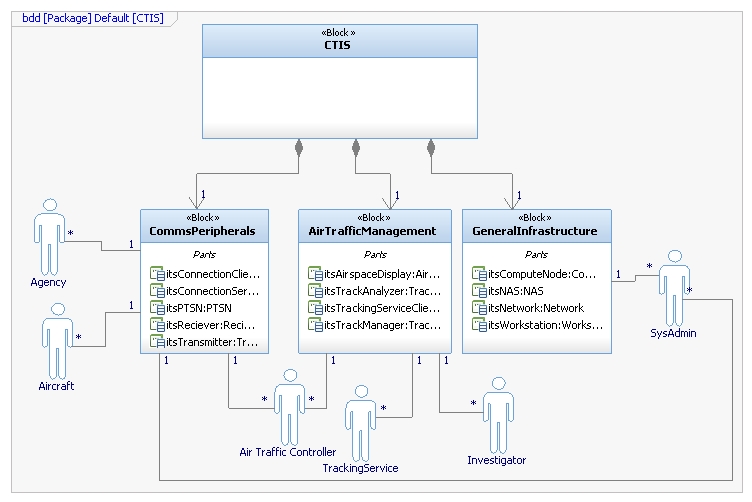
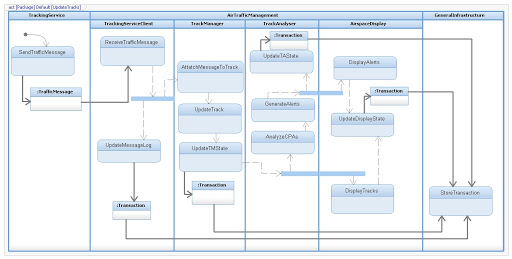
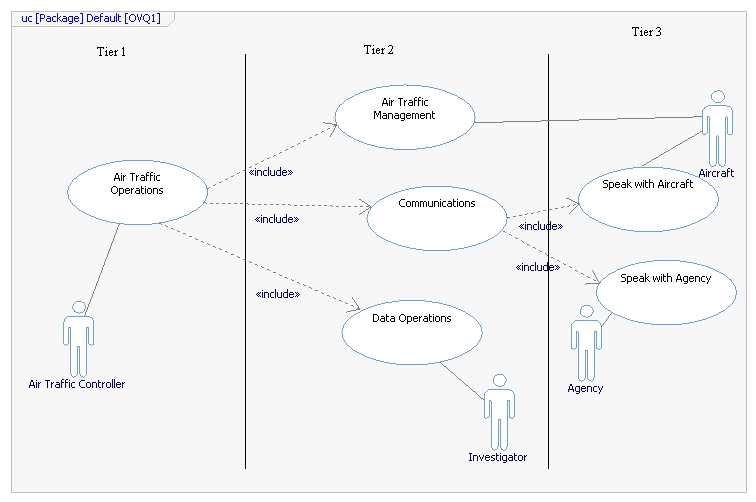
One week midterm assignment to develop an air-traffic control communications and data concept.
Eclipse>Papyrus (SysML/UML)
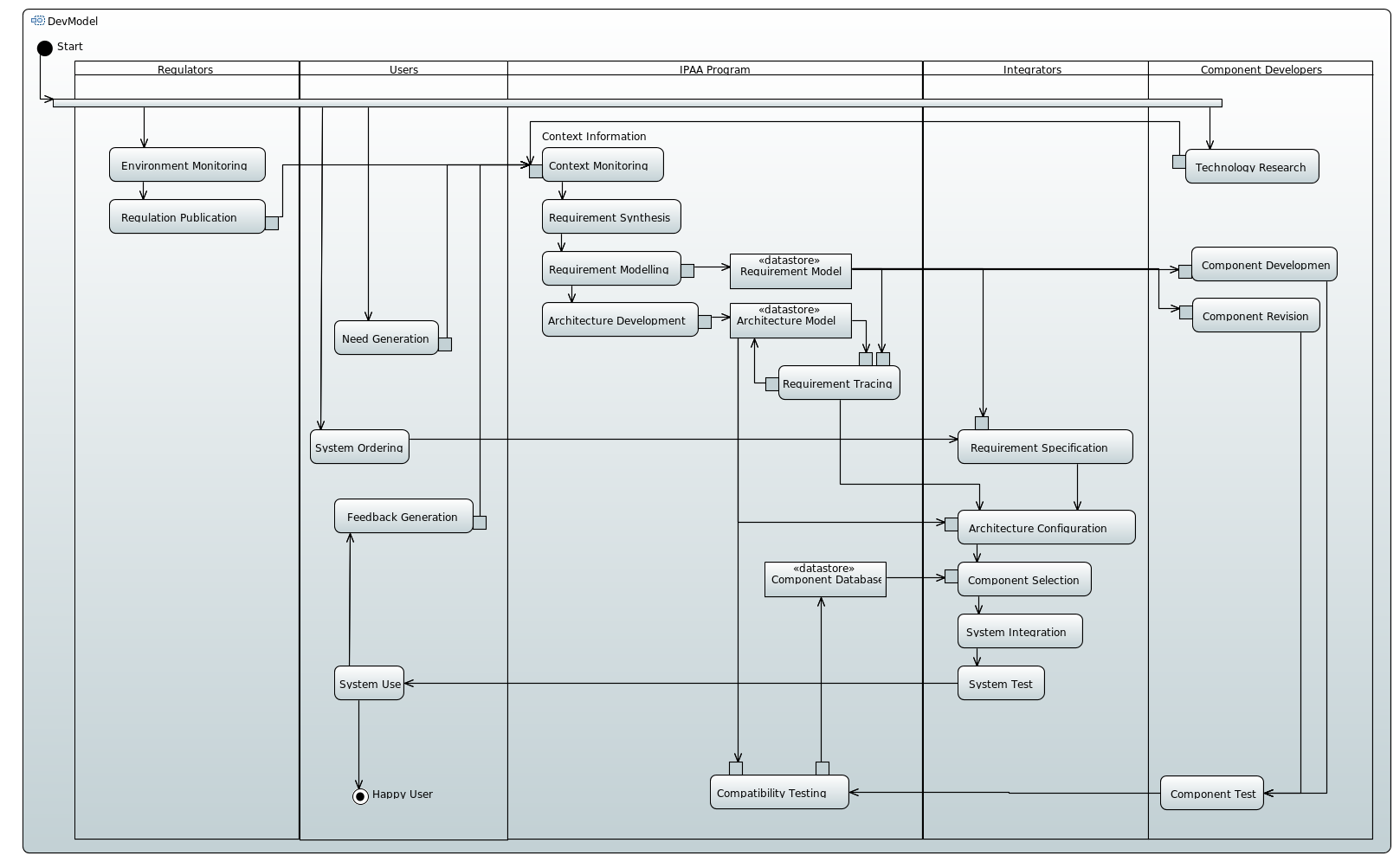
Activity Diagram for IPAA Enterprise made in Papyrus
Solidworks Motion Simulation
Bulldozer attachment for a Case 446 tractor.
Modelling and Animation in Blender
Geologic sample holder modelled for 3D printing in Blender and animated.

John Kha
Systems Engineer, Naval Officer
Request access to contact information, project papers and more.